Image: AMD
It was only a matter of time before security vulnerabilities started appearing for AMD processors.
Graz University of Technology researchers have discovered two new side-channel attacks – “Collide+Probe” and “Load+Reload” – that affect AMD CPUs from 2011 to 2019. These would include recent Zen products such as the Threadripper 2970WX (Zen+), Ryzen 7 3700X (Zen 2), and EPYC 7571 (Zen).
Image: Graz University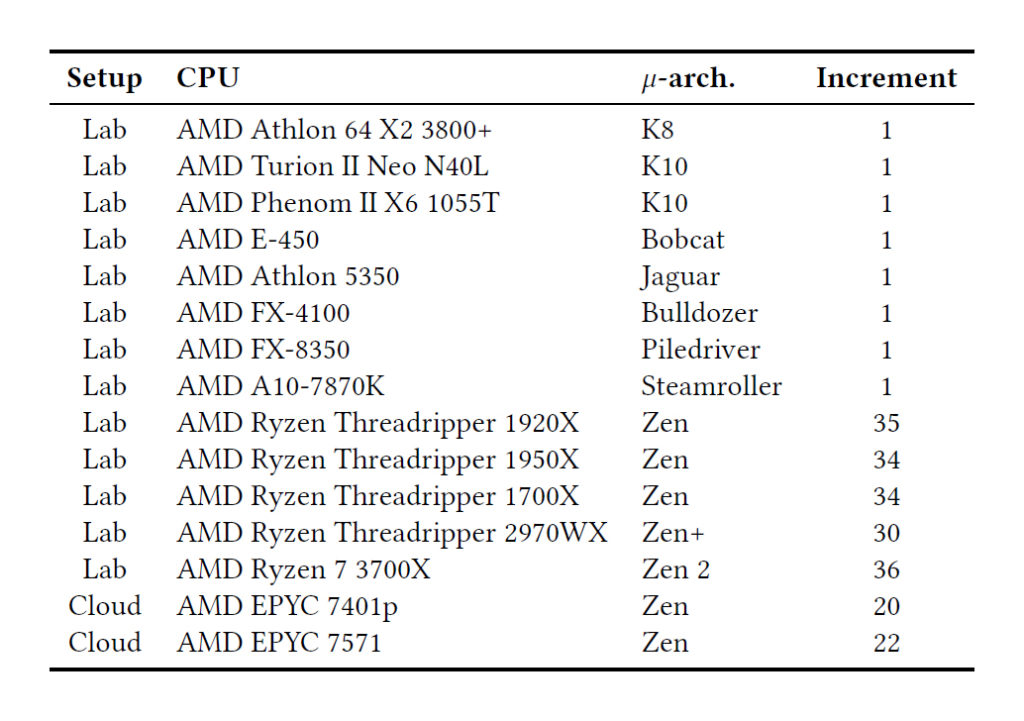
Both vulnerabilities involve AMD’s L1D cache way predictor, which enhances performance and reduces power consumption by managing how cached data is handled within memory. They could allow attackers with physical access to steal sensitive data.
Collide+Probe lets an attacker “monitor a victim’s memory...
Continue reading...
Last edited by a moderator:
